Greetings, Cyber Defenders! Prepare to explore vulnerability scanning with the OWASP Zed Attack Proxy (ZAP). Vulnerability scanning is critical in cybersecurity, and ZAP is a strong tool for extensive testing, popular among those looking to thoroughly examine web applications.
In this lesson, we'll walk you through ZAP setup, basic features, and a brief comparison with Burp Suite. You'll learn about spidering, passive and active scanning, as well as how to get started with ZAP and maximize its capabilities.
If you're eager to learn about ZAP's capabilities, let's jump in together. Let the journey begin!
What Is ZAP?
Zed Attack Proxy (ZAP) is an open-source penetration testing tool that was previously known as OWASP ZAP. It's a versatile tool used by penetration testers, bug bounty hunters, and developers to scan web programs for security flaws throughout the testing phase.
ZAP has several functionalities, including active and passive scanning, as well as API testing capabilities.
It is fundamentally a middleman manipulator. It displays all of the queries you make to a web app as well as the responses you receive from it, allowing you to spot vulnerabilities and potential attack vectors in real-time.
ZAP assists you in understanding how the application behaves in various circumstances and conditions by intercepting and altering traffic between your browser and the web application.
ZAP can be installed on Windows, Linux, and macOS. Docker images are also available. We will demonstrate how to install it on Kali Linux.Setting Up Your Zed Attack Proxy on Kali Linux
Let's go through the entire process of getting ZAP up and running.
Installing ZAP on Kali Linux
ZAP is not installed in Kali's current version, 2024.1, as of this writing. It is, however, easy to install.
Before installation, always update the repositories to ensure the most recent version is installed by executing:
sudo apt update—y.
Once finished, you can install ZAP with the command:
sudo apt install zaproxy
Setting Up Your Proxy
You do not need to configure a proxy for your browser, such as FoxyProxy, as in Burp Suite, because ZAP handles everything.
The "Browser Launch" option is automatically setup to use ZAP and disregard certificate warnings, making it much easier to get started without changing any settings. This allows you to instantly begin testing web applications for vulnerabilities without any further setup or configuration. Simply start ZAP and you'll be good to go.
However, if you wish to utilize any of your browsers with an existing profile, such as other browser add-ons installed, you must manually setup your browser to proxy through ZAP and import and trust the ZAP Root CA Certificate.
We’ll show you how to set this up on Firefox in Kali.
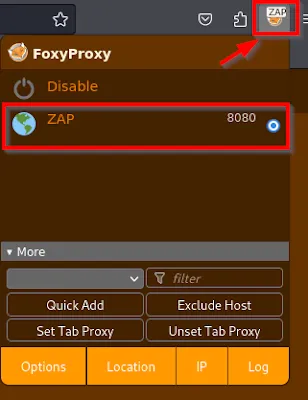
The first thing you need to do is download the FoxyProxy add-on.
Next, open FoxyProxy so we can configure it.
From here, head to the proxies tab and enter the following information.
- Title: ZAP
- Type: HTTP
- Hostname: 127.0.0.1
- Port: 8080
Once finished, click “Save.”
When you want to proxy traffic using ZAP, go to the add-on and pick "ZAP."
Install ZAP Certificate
If you do not utilize ZAP's built-in browser feature, you will need to manually configure the certificate in your browser. If you try to access any SSL/TLS site using a browser other than ZAP, you must configure it to utilize ZAP's CA root certificate to avoid certificate errors.
ZAP suggests that you run your browser from the "Quick Start" area, but if you prefer to configure it manually, here's how to install the certificate. We're installing it in Firefox.
To begin, navigate to http://zap with ZAP running and FoxyProxy enabled for ZAP usage. Once there, select "Download" to save the certificate to your PC.
Now, in your Firefox search bar, type about:preferences and hit enter. This will take you to the Settings page. Search for "Certificates" and select "View Certificates."
The "View Certificates" button displays all of your trusted CA Certificates. You can import a fresh ZAP certificate by choosing "Import" and selecting the downloaded file.In the popup, select “Trust this CA to identify websites,” then click OK.When we enable the ZAP Proxy, we can intercept any encrypted traffic.
Now that everything is in place, we'll guide you through some of ZAP's features. ZAP offers several tools, but we won't be able to cover them all here. We will show you a few to get you started.
Starting ZAP
ZAP may be started in Kali in two ways: by typing zaproxy in the terminal or by selecting it from the applications menu under "Web Application Analysis."
When you start ZAP, a screen will appear asking, "Do you want to continue this ZAP session?"Persistence will save everything to an HSQL database, which you can then inspect or reload into ZAP to see all of the request history, site information, and so on.
We'll be choosing "No, I don't want to continue this session at this time."
ZAP Overview
Before we begin using ZAP, let's look at the main interface and illustrate where some of the essential functions are situated. The interface is dense with information, but keep in mind that ZAP is capable of numerous tasks.
- Menu Bar: Here, you can create and manage sessions, create reports, find tools, get help, and more.
- Toolbar: Includes buttons that provide shortcuts to the most commonly used features.
- Tree Window: Displays the hierarchical view of the site you are testing and the script tree.
- Quickstart/Workspace Window: This is a quick and easy way to use ZAP, especially if you’re new. It also displays requests, responses, and scripts you can edit.
- Information Window, including:
- History tab: This shows a log of all the HTTP requests and responses sent and received through ZAP.
- Search Tab: This allows you to search through the requests and responses.
- Alerts Tab: Displays security alerts found during the scans.
- Output Tab: Provides detailed output from various scans and processes.
- Footer: Displays ZAP status information.
- Alerts Counter: This displays a summary of the alerts found. It’s color-coded (like red, yellow, etc.) to represent the severity of the alerts found during the scanning process.
- Main Proxy: This is the main proxy configuration that ZAP uses, which is set to "localhost:8080."
- Current Scans: This section displays any currently running scans, with icons indicating their status or progress.
Update Add-ons
Before you begin using ZAP, make sure to check for and update any necessary add-ons. This guarantees that you have the most current experience.
To check for updates, use CTRL + U, or use the toolbar shortcut.
This will launch the installed add-ons. Each add-on is labeled with its version number and a brief description of its function. If a newer version of an add-on is available, "Update" will appear to the right of the description.
You can choose which ones to update individually, but it is recommended to update everything at once.
To trigger the update, choose any add-on and click "Update All".
ZAP Tips
Before we begin, here are some pointers to remember when using ZAP.
Right-click anywhere to see what alternatives are available.
If you need help, you can use the thorough ZAP user guide found by pressing F1.
ZAP Spidering
The first tool we'll demonstrate is the usual spider in ZAP. This spider crawls web pages and looks for links to other pages in the same web application. This recursive process continues as long as new links are detected.
The spider creates a site tree and displays all of the pages found.
This spider is relatively fast and can be utilized for ordinary applications. However, you should consider employing this spider with the AJAX spider in more recent apps.
To launch Spider, pick "Spider" from the "Tools" menu or use the CTRL + ALT + S keyboard shortcut.
In the following window, enter the URL of the web app you're spidering and click "Recurse." This instructs ZAP to crawl all URLs or directories starting with the specified URL.
When you're ready, choose "Start Scan."
Once the spidering is complete, you will see all of the nodes discovered for the web app. The lower-right corner displays "Nodes Added: 69," which indicates how many new objects the Spider discovered and added to the Sites tree during its crawl.
ZAP AJAX Spidering
More current apps employ JavaScript, which the conventional ZAP spider does not fully grasp.
Here's where the AJAX spider comes in. This spider opens a browser, clicks on objects, and even fills out forms, providing you with a more detailed overview of the web app. It attempts to mimic a user's behavior when engaging with the program.
This spider is much slower than the conventional one, but it performs much better with current programs.
To launch the AJAX spider, utilize the "Tools" menu or the keyboard shortcut CTRL + ALT + X.
Here, you may choose the URL of the app you wish to test as well as the browser that the spider will use. Firefox, Chrome, and Safari are among the available options.
You can also provide advanced settings. When you're ready, choose "Start Scan."
Once the scan is complete, any discovered nodes will be displayed in the site tree area, accompanied by a red spider. The AJAX spider crawled 1103 URLs against the normal spider's 116.ZAP Scanning
Before we show you ZAP's scanning functionalities, remember that you should only use ZAP's active scanning to attack an application with explicit permission to test.
Passive Scanning
Passive scanning is simply looking at the raw requests and answers. ZAP does not perform anything; it just monitors the traffic that passes through it. It examines this traffic to discover potential vulnerabilities without initiating any new queries.
Passive scanning is safe for usage in any web application.
When you spider a website, ZAP runs a passive scan and displays any alerts in the "Alerts" tab.
In the following part, we will take a closer look at these alerts.
Active Scanning
Active scanning seeks out more vulnerabilities by employing known attacks against the chosen targets. It only detects specific vulnerabilities, such as XSS, SQL injection, buffer overflows, Log4Shell, and remote file inclusion.
The Active scanner does not detect logical vulnerabilities, such as faulty access control.
You can specify scan policies, but we won't go into detail here. These rules allow you to define a threshold for the number of concerns raised, and the strength options control the amount of attacks per parameter.
You may configure the options for active scanning, just like you can with most ZAP programs. These include the number of hosts scanned concurrently, the maximum scan length, and whether to handle CSRF tokens.
Select "Automated Scan" from the quick start menu to begin.
This will bring up the automated scan launch screen. You'll enter the URL and select the spider and browser you want to use. When you're ready, select "Attack" to begin.
Once the scan is complete, you can view all of ZAP's notifications in the "Alerts" page.As shown in the graphic above, ZAP discovered 28 vulnerabilities classified by severity: high (red), medium (orange), low (yellow), and informational (blue).ZAP displays the number of vulnerabilities it has detected. Let's examine more closely at the SQL injection. Select the arrow next to it to show where the problem was discovered in the application. Then, select the URL to view more information about the warning.
ZAP delivers a lot of information. The URL of the alert, as well as its risk and confidence level, are displayed in the right side. Common software security vulnerability lists will also include a CWE and WASC ID. Each vulnerability has its unique identification number.
Next, you’ll see a description of the alert and how ZAP confirmed this alert. It notes the attack method used ("AND 1=1 --"). You'll need to validate this to see if the vulnerability really exists.
It also provides a potential solution: do not trust client-side input and utilize server-side validation, such as prepared statements, to reduce the risk.
Conclusion
In this engaging ZAP tutorial, we dived into the depths of cybersecurity expertise. From its powerful capabilities to the art of web app testing, we've created the groundwork for your path to expertise.
As you explore ZAP's extensive capabilities, keep it updated to remain ahead of developing threats. OWASP ZAP is more than simply a tool; it is a sentinel that enables cybersecurity warriors to strengthen defenses and prevent exploitation.
Our voyage may be over, but the quest for cyber resilience continues. Keep watchful, keep informed, and let us work together to navigate the ever-changing cybersecurity situation. Thank you for joining us on this fascinating journey.
Stay Informed, Stay Safe!