Purpose
Main motive of this web audit is to
scan and discover security vulnerabilities in a well-known
website where undergraduates have to
relate their academic knowledge into a reality security
audit. We were advised to use Automated
as well as manual testing for this security web audit.
The following tools were used to check
the vulnerabilities using the automated method
dotdotpwn, uniscan, nikto, sublist3r, D-TECT,
wafw00f and Nessus, Nmap and Owas zap.
Abstract
Cybercrime, misrepresentation and information break are danger
comprising extraordinary
dangers to associations. A ton has been lost and organizations
need to discover systems to stop
the dangers from really developing and deflect further
misfortunes. This exploration inspected
the systems associated with IT security web audit and how an web
audit can improve organizations' IT security .The examination estimated IT
administrators and workers' attention
to cybercrime hazards; estimated their knowledge of IT security
audit norms and rules; and
estimated the effect of IT security audit on association's
development. This investigation
utilized an organization as a contextual analysis, assessed the
flow IT security audit status of the
organization and decided the adaptability for development of IT
security audit strategy and
system .A quantitative exploration was done to acquire
cybercrime information and assemble
more thorough data about the topic. This investigation
unmistakably indicated that IT security
audit is basic for the improvement of any association that
utilizes IT.
Introduction
Cybercrime is a danger that is
confronting each association and there is a developing worry on
the most proficient method to counter
it. Every day, cybercrime hits associations' data
frameworks and causes them injury, huge
money related misfortune and notoriety harm. There
is no spot to be smug.
A cybercrime can assault your business'
data framework whenever and you positively disdain
the possibility that your association's
information will be penetrated like over 43% of digital
assaults target independent venture 64%
of organizations have encountered Web attacks. 62%
experienced phishing & social engineering
attacks. 59% of organizations experienced vindictive
code and botnets and 51% experienced
forswearing of administration assaults .A superior data
framework security is urgent to ensure
an association's IT against cybercrime,
misrepresentation and information break.
It is the obligation of each association to guarantee
that the association's information is
secure, secret and its trustworthiness isn't undermined.
The security of an association relies
upon the client rehearses, the product and the data taking
care of cycles. In any case, how might
association realize what ought to be secured and by what
means would it be a good idea for it to
be ensured? Where should the association start from?
Web Security auditing, this is the place
everything starts. Albeit some writing states that web
security auditing, is a fundamental
advance in ensuring association's data framework against
Cybercrime, misrepresentation and
information penetrate ought to be completed consistently,
as an orderly assessment by a free
master on adherence, to find a shortcoming in the
association's IT . Does an IT security
audit truly help the association to improve the data
security and moderate potential network
protection hazards? This examination report will
introduce the way and the method used to
accomplish an effective Web security audit and will
analyze if the strategy assists with
improving the IT security or not. To accomplish this
objective, I will examine the current
auditing technique of some Linux frameworks in the
targeted international site Gitlab.com.
At that point an IT web audit program
for those frameworks, as indicated by the business
norms and rules, lastly actualize the
audit program and issue an audit reports that incorporates
the discoveries and the subsequent moves
that ought to be made so as to moderate potential
data security hazards. Actually, IT
auditing requires noteworthy assets including time and cash.
In any case, the expense of a
Cybercrime, misrepresentation or information break can be high
surely. Hence it pays to forestall it
The principle point of this examination is to introduce the
significance of web security audit and
to inspect the advantages of IT security auditing measure
as a significant apparatus in improving
the association's data security .Furthermore, the
exploration researches how the
association's attention to cybercrime hazards, how well they
utilize worldwide security norms and
rules and how they are performing IT security audit
routinely. A case of gitlab a website is
used to analyze and test a web security audit.
Automated Testing
Vulnerability Scanning Tools and Relative Screenshots of the Results
1. DotDotPWN
DotDotPwn is a keen fluffing device that empowers an assailant to
spot potential
weaknesses that might be identified with navigate index inside a
given help. The
device is compelling and can help find imperfections in web server
conventions like
TFTP, HTTP, and FTP. The apparatus can especially be valuable when
dealing with
infiltration tests on applications that are online.
DotDotPwn is an aspect of the Kali Linux bundle, thusly it comes
pre-introduced.
Back Track Linux being an archetype of Kali has incorporated this
apparatus as the
primary Mexican tool. This device is composed and programmed
utilizing Perl
language.
As a fluffing device, DotDotPwn is entirely adaptable and is
likewise ready to send
some elevated level insight when executing fluffing activities. It
very well may be
utilized by programmers on web stages like ERPs, CMSs, and so on
It has a stunning
element which permits it to run a module that is convention
autonomous. Through
this, you can without much of a stretch convey a payload to a host
utilizing a
particular port of your decision.
By applying the STDOUT module it can likewise help with scripting
tasks. Because of
having amazing highlights, this instrument is truly adept at
computerizing fluffing
activities. By utilizing it you can recognize a portion of the
escape clauses that can be
abused during an assault. DotDotPwn can be utilized to spot
mistakes that may
happened because of inappropriate information approval, boundaries
that are
wrong or information that is mistaken. Such sort of information
can assist the
aggressor with realizing which kind of assault payload to convey
to the person in
question. Because of the device's many use cases, it can give a
few assault vectors
which can be exploited during an assault.
How it works?
Like most fluffing instruments DotDotPwn
works by stacking a lot of information
stages into the focused on
administration. Subsequent to contributing the
information the apparatus will keep an
eye on how the program being assaulted
gives a reaction. Contingent upon the
input gave by the program DotDotPwn can
regard the data as vulnerability.
Sometimes vulnerabilities are spotted
when the information stacked into the
program makes it crash or give yields
that may appear to be superfluous. When
conveyed on a site the device can permit
the assailant to see the status of the HTTP
demand for each payload that is being
tried. Through the status input the aggressor
can have the option to know whether the
site being tried is helpless.
Screen Shots
I. When the program starts
|
II. Ping command to find the IP address III. After we start the scan it is refused because of the website has a webserver which is https. |
subdomains of sites. It helps pen-analyzers in gathering and assembling subdomains
for a space which is their objective. So as to bring the precise outcomes, sublilster
utilizes many web indexes like Google, Yahoo, and so forth and even apparatuses
like Netcraft, Virustotal, and so on.
Screen Shots
I. First the tool is downloaded using the git clone command
and then we run
the sublist3r python file to find the
subdomains and the total number of
them. In this case it is 184 sub
domains.
against web workers for different things, including more than 6700 conceivably
perilous documents/programs, checks for obsolete adaptations of more than 1250
servers, and form explicit issues on more than 270 servers. It likewise checks for
server design things, for example, the presence of various record documents, HTTP
server choices, and will endeavor to recognize introduced web servers and
programming. Sweep things and modules are habitually refreshed and can be
naturally refreshed.
Nikto isn't planned as a subtle apparatus. It will test a web server in the speediest
time conceivable, and is clear in log documents or to an IPS/IDS. Be that as it may,
there is uphold for LibWhisker's enemies of IDS strategies on the off chance that you
need to check it out (or test your IDS framework).
Few out of every odd check is a security issue, however most are. There are a few
things that are "info only" type watches that search for things that might not have a
security defect, however the website admin or security architect may not know are
available on the worker. These things are normally stamped properly in the data
printed. There are additionally a few checks for obscure things which have been
seen examined for in log documents.
Screen Shots
I. The first scan did not specify any options, It was a normal scan on the targetted site.


III.Then we scan the number 4 option for the injection command 
4. Uniscan
Uniscan is a straightforward web weakness scanner that looks for
regular blemishes Screen Shots I. First we enter the command uniscan to get the options. II. Then we do a quick scan by using the –u and enter the IP or the URL III. Then we specifically
mention many options and continue to scan which will
IV. Here we have the directory we obtain which is a common vulnerability for every take time in this case it took 36 hours. The command used was uniscan –u https://about.gitlab.com/ -qweds website, Cannot be straight away used to exploit. an attack. VI. This where we found some information of the website which are external hosts found. In this case 9265 URLs were found.
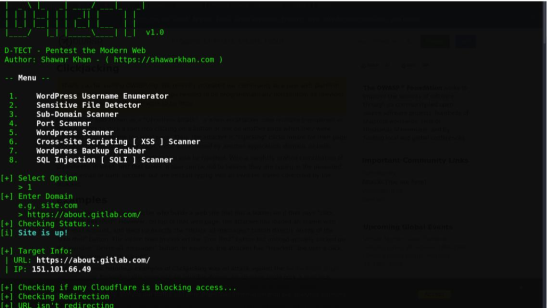
5. D-TECT D-TECT is an All-In-One Tool for Penetration Testing. This is
exceptionally modified
Similarity:
Requirements for the scanner:
Features of the scanner :
Select the ideal checking capacity
(module) by choosing its succession number. For Screen Shots I. In this
scanner the git clone command is used to download the
scanner and
scan and gave a result of 2 open ports. V. Now
we run the 5th , 6th ,
7th and 8th option
which is the word press scanner, XXS scripting, wordpress backup generator and SQL injection. Which gave a result of not vulnerable, but highlighting the vulnerability of click jacking
Commonly, clickjacking is performed
by showing an undetectable page or HTML component, inside an iframe, on head of
the page the client sees. The client accepts they are tapping the noticeable page yet
truth be told they are clicking an imperceptible component in the extra
page translated on head of it. The imperceptible page could be a
malevolent page, or an authentic page the client didn't expect to visit – for instance, a
page on the client's financial site that approves the exchange of cash. There are a few varieties of the
clickjacking assault, for example,
1. Likejacking – a procedure where the
Facebook "Like" button is controlled, Solutions to Prevent this Attack There are two general approaches to protect against clickjacking:
6.Wafw00f (SCANNED A HIGH LEVEL VULNERABILITY P2 ) Web Application firewalls are ordinarily firewalls taking a shot at the application layer which screens and alters HTTP demands. The key contrast is that WAFs chip away at Layer 7 – Application Layer of the OSI Model. Essentially, all WAFs secure against various HTTP assaults and questions like SQLi and XSS. Since the firewall can distinguish HTTP techniques, SQL inquiries and different contents put as contribution to various structures in a site, it can sift through the solicitations simply like an ordinary firewall would do. One can actualize an arrangement on what ought to be allowed and what not as contribution through a site. A WAF will be regularly present in a web application where there is Strict Transport Security empowered like a financial site or an internet business site. While directing a pentest, identifying the waf goes under recon, and planning the web application design. One ought to distinguish the presence of a WAF and assess it if there should be an occurrence of a Black Box testing. This has a significant impact in deciding the techniques to continue during a Web-Application Penetration Test. Wafw00f is essentially a python apparatus which computerizes a lot of methods utilized in finding a WAF. Wafw00f basically questions a web worker with a lot of HTTP demands and strategies. It investigations the reactions from them and distinguishes the firewall set up. Screen Shots I. First when we run the wafw00f without a URL it shows the below message II. When we run the wafw00f with the targetted URL we can see that the web application has no WAF. Which is a critical vulnerability. Because WAF reduces the attacks by 20%.
Solutions
– A WAF or Web Application Firewall ensures web applications by sifting
and observing HTTP traffic between a web application and the Internet. It commonly shields web applications from assaults, for example, cross-website
phony, cross-webpage scripting (XSS), record consideration, and SQL infusion, among others. A WAF is a convention layer 7 protection (in the OSI
model), and isn't intended to safeguard against a wide range of assaults. This
strategy for assault relief is normally important for a set-up of devices which
together make an all-encompassing safeguard against a scope of assault vectors.
so using cloudfare or AWS firewall will defend these attacks.
Screen Shots7. NMAP (LOW P4 and informational P5)
Nmap ("Network Mapper") is a free and open source
(permit) utility for network I. First we ran the command nmap www.gitlab.com –v
we found many open  II. When we scanned port 80 specifically we weren't able to find any specific information. III. When we scaned using the command nmap
-v –A 172.65.251.78
It shows another websites IP which
is vulnerable for the other site because of
this website.
shows the IP adrees of a another website
. It can be used to do tunneling and clickjacking attacks for example. 8. Nessus (SCANNED FOR INFORMATION P5)
Nessus is a far off security filtering apparatus, which examines a
PC and raises an Screen Shots I. First
we download and run nessus using the command /bin/systemctl
start II. After log in to the nessus we have to enter the IP and then start
the scan III. After the
scan is complete it will display as shown below. V. Next when we click vulnerabilities we can see the ports and web servers information
one by one which falls under the informative category.
9.
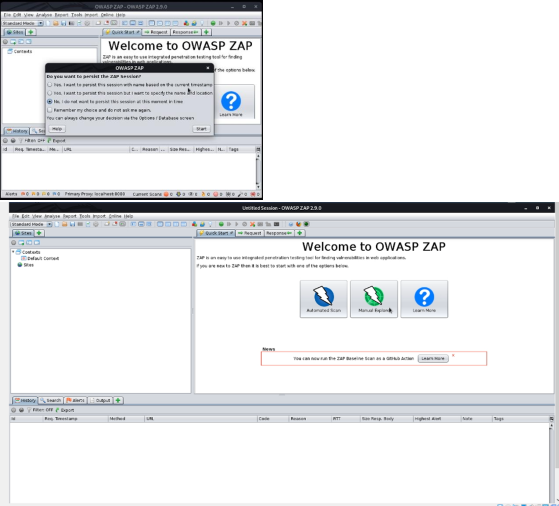
OWASP ZAP OWASP ZAP (short for Zed Attack Proxy) is an open-source web application
security scanner.When utilized as an intermediary
worker it permits the client to control the entirety of the traffic that goes
through it, including traffic utilizing https. It can likewise run in a daemon mode which is
then controlled by means of a REST API. The scanner includes : Intercepting
intermediary worker, Traditional and AJAX Web crawlers, Automated scanner, Passive
scanner, Forced perusing, Fuzzer, WebSocket uphold, Scripting dialects, and
Plug-n-Hack uphold. It has a module based engineering and an online 'commercial
center' which permits new or refreshed highlights to be included. The GUI
control board is anything but difficult to use. Screen Shots I. We select the automated scan III. After several hours of scanning it will show some information for example here the highlighted section shows the pasasword files
which is very informative for an attacker.
Manual Testing 1. Before we enter the password the system requires a password with a minimum length of 8 characters. which is great eventhough it will be hard for the user to remember the password. 2. Even if a intruder wants to change the password of the victim it requires the old password to change it. which is helpful eventhough the user forgets to log out.
SQL injection is a web security weakness that permits an aggressor to So if the accurate security measures were not taken to stop SQL injection attack the Select Query will be – SELECT * FROM users This makes the underlined part a comment consequently because “OR
1 = 1” 4. Broken authentication or brute force attacks According to our targeted website when we perform a brute  After some wrong attempts of entering passwords it checks whether
you’re human which means the website is invulnerable to brute, dictionary force or other automated attacks. 5. When we
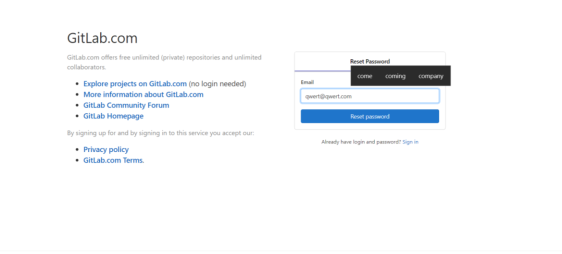
try to reset the password it asks for an email and after we enter the email we
will be shown a message saying “If your email exist in our database we will send you the reset link”. Which shows that there is a powerfull security infrastructure behind then doors eventhough they spill out some information. |
Conclusion
This exploration has
zeroed in on the significance of IT web security reviews as the significant
cycle in associations that assists with improving the data security and ensure
the business' information against cybercrime, misrepresentation or
information penetration. Although the website can be yanked a little, we should
minimize the medium level threats found which will increase the security of the
website.
A contextual investigation of a website found that while there are various by
and
large information and may not be ideal, leaving workers helpless against
cybercrime dangers, assaults and misrepresentation. Various security goals were
settled by the security infrastructure of an organization in this case the git
lab
security hub, during the review cycle to improve the entrance control and the
weakness of the frameworks. From this examination, it tends to be inferred that
IT web security audit review is an essential movement that each IT association
must make arrangement for and complete web security protection.
- https://www.youtube.com/watch?v=CWo_mjNjrjA
- https://www.tarlogic.com/en/cybersecurity-services/web-audit-owasp-web-security-audit/
- https://securitytrails.com/blog/open-ports
- https://resources.infosecinstitute.com/14-popular-web-application-vulnerability-scanners/
- https://tools.kali.org/information-gathering/nikto
- https://www.wonderhowto.com/
- https://www.hacking.land/2016/08/d-tect-pentesting-modern-web.html?m=1
- https://www.hackingloops.com/d-tect/
- https://kalilinuxtutorials.com/wafw00f/
- https://www.atlassian.com/software/confluence/free?utm_source=gdn&utm_medium=paiddisplay&utm_campaign=P:confluence|O:ppm|V:gdn|G:row|L:en|F:aware|T:lookalike|A:image|D:desktop&utm_c ontent=P:confluence|O:ppm|V:gdn|G:row|L:en|F:aware|T:lookalike|A:image|D:desktop|U:lookalike-confluenceeval_knowledge_align_728x90&gclid=CjwKCAjw_sn8BRBrEiwAnUGJDrNRm3eY6ElGIpVpjCvF0kjc1rXAjmd7Vsk4y9i4 0OgVrTLK5QwN8xoCgGcQAvD_BwE
- https://tools.kali.org/information-gathering/nmap
- https://en.wikipedia.org/wiki/OWASP_ZAP
- https://www.cybintsolutions.com/cyber-security-factsstats/#:~:text=43%25%20of%20cyber%20attacks%20target,experienced%20denial%20of%20service%20attacks.
- https://tools.kali.org/informationgathering/sublist3r#:~:text=Sublist3r%20is%20a%20python%20tool,Bing%2C%20Baidu%2C%20and%20Ask.
- https://www.cloudflare.com/learning/ddos/glossary/web-application-firewall-waf/
- https://www.csoonline.com/article/3032743/web-application-firewall-a-must-have-security-control-or-anoutdated-technology.html
- https://portswigger.net/web-security/sql-injection
Stay Informed, Stay Safe!